Navigating Cyber Threats: Ukrainian Lessons on Safeguarding eCommerce Businesses
As the digital marketplace continues to expand at an impressive rate, cybersecurity has emerged as a critical consideration for businesses across the globe. Juniper Research indicates that by 2023, online scams are predicted to cause worldwide losses totaling a staggering $48 billion, with Europe being a prime target for such cyberattacks. The events of 2022 underscored this risk, urging businesses to emphasize their cybersecurity efforts more strongly.

The trials faced by Ukraine offer invaluable insights for companies striving to safeguard their eCommerce operations from a wide array of risks. The country endured several cyber-attacks in 2022, leading to substantial financial damages for businesses and individuals.
The government's response was to initiate an online security awareness campaign to educate its populace on cyber safety and equip them with essential tools and resources to shield themselves. This involved advocating for two-factor authentication, the implementation of firewalls, regular software updates, and diligent monitoring of online activities.
eCommerce Security: A Snapshot from Ukraine
Studies demonstrate that over the previous five years, Ukraine's online commerce market has multiplied five-fold, amounting to $4 billion by 2020's conclusion, which translates to 8.8% of the total retail turnover. This marked growth can be attributed to an increasing consumer base opting for online shopping platforms, complemented by the increasing accessibility and affordability of technology.
However, the war erupted in Ukraine in 2022 led to considerable financial setbacks for numerous companies due to the physical damage inflicted on warehouses and in the context of eCommerce security, larger eCommerce enterprises remained unscathed by the war, thanks to the comprehensive measures they had taken to mitigate security risks.
These precautionary actions encompassed recognizing eCommerce security as a critical aspect of business operations and housing servers in locations outside Ukraine. Such strategies allowed these companies to shield their online storefronts from threats, unlike public firms and infrastructure providers who fell victim to severe DDoS attacks.
This instance is a poignant testament to robust eCommerce site security's crucial role for businesses operating in volatile environments. It underlines that investments in eCommerce security can equip businesses, particularly online stores, to safeguard their assets and maintain operational continuity amidst crises. Thus, companies must prioritize resolving eCommerce security challenges to lessen the potential repercussions of future events that could jeopardize their operations.
Global eCommerce Security: The Repercussions of the 2022 Cyber Offensives
2022 will be remembered for a string of destructive cyber onslaughts, targeting some of the world's most prominent enterprises.
The LastPass Security Breach
One of the most notorious events involved LastPass, a personal password management firm boasting over 33 billion users. Despite its standing for exceptional security, it faced two breaches within a single year, compelling online retailers to contemplate the potential damage their businesses could have sustained.
The Cyber Intrusion at Okta
An equivalent scenario unfolded at Okta, an enterprise specializing in devising IDM systems to fortify user authorization. Unlike LastPass, serving chiefly the corporate sector, Okta's client spectrum is considerably broader, leading to breaches for Fortune 500 companies relying on Okta to secure their confidential user account details and client data.
These high-visibility breaches underscore the cruciality of rigorous security protocols for eCommerce businesses, irrespective of size.
Without adequate security procedures, companies risk eroding client trust and exposing themselves to financial fraud due to breaches, not to mention tarnishing their reputation. With the continuous growth of the eCommerce landscape, the imperative for online enterprises to prioritize website security and implement necessary protective measures is more pronounced than ever.
Why Does eCommerce Security Hold Paramount Importance Now?
The eCommerce domain is broad and ceaselessly growing, with sales reaching an impressive 5.7 trillion dollars in 2022 and projections estimating a rise to 8 trillion dollars by 2026. With such an astonishing sum in play, it's hardly surprising that cybercriminals are increasingly setting their sights on eCommerce platforms for monetary gain.
While one could conjecture that this money is dispersed across innumerable online businesses, the actuality is far more alarming. As cyber criminals persistently discover and exploit weaknesses in eCommerce platforms, they could employ the same strategies to breach thousands of other stores employing similar software. A single security compromise could pave the way for subsequent attacks.
This stark reality is one that eCommerce sites need to confront. In truth, website security is no longer optional for online businesses; it's a requirement. As the eCommerce sector continues to burgeon, so will the security threats it encounters.
Hence, eCommerce enterprises must remain alert and preemptively shield themselves from cyber threats. This entails regular software updates, robust security protocol enforcement, and vigilant monitoring of suspicious activities.
Neglecting cybersecurity is no longer viable for eCommerce sites. With the stakes higher than ever, online businesses must adopt necessary measures to safeguard themselves and their clientele.
The First Step in Formulating an eCommerce Security Strategy
In an increasingly digital world, security threats loom large for every eCommerce site. This threat is especially acute in eCommerce, where online stores harbor valuable customer data and financial details, making them enticing targets for hackers.
It's essential to realize that securing your business from hacking isn't a one-off task; it's a continuous process. Past strong protection for an online store doesn't assure enduring security. Cybercriminals continually innovate their attack methods, demanding businesses to maintain constant vigilance.
Specialists propose a three-fold approach to counter the relentless security threats: prevention, regular upkeep, and specific protective measures.


Proactive Measures for Cyber Security
With the burgeoning growth of e-commerce enterprises, data protection, and cyber security have become paramount. One of the fundamental measures e-commerce outlets can adopt to shield themselves from cyber threats is compliance with the Payment Card Industry Data Security Standards (PCI DSS).


These protocols serve as an industry standard for data security, offering guidelines for entities that process credit card transactions. Adherence to these standards can significantly bolster the security posture of any e-commerce establishment.
These protocols serve as an industry standard for data security, offering guidelines for entities that process credit card transactions. Adherence to these standards can significantly bolster the security posture of any e-commerce establishment.
The 12 requirements of the Payment Card Industry Data Security Standards include the following:
-
Establishing and sustaining a firewall configuration to safeguard cardholder data
-
Avoiding vendor-supplied defaults for system passwords and other security parameters
-
Safeguarding stored cardholder data
-
Encrypting cardholder data transmission across open, public networks
-
Ensuring all systems are protected against malware and regularly updating antivirus software or programs
-
Developing and preserving secure systems and applications
-
Limiting access to cardholder data based on business need-to-know
-
Assigning a unique ID to each individual with computer access
-
Limiting physical access to consumer data
-
Monitoring and tracking all access to network resources and cardholder data
-
Regularly testing security systems and processes
-
Maintaining a policy addressing information security applicable to all personnel
Due to the war, Perspective's team is geographically scattered across various parts of Ukraine and Europe, with many individuals working remotely and employing numerous communication channels.
While the conflict in Ukraine may have introduced added complexities for businesses operating in the area, implementing the appropriate tools and best practices can help fend off attacks and ensure the ongoing prosperity of e-commerce operations.
Management of Secure Access
Establishing guidelines for access transfer and utilizing multiple channels for communication and login credentials is crucial. For instance, transmitting a temporary password through a distinct channel can add another layer of protection.
An alternative method involves using a password repository system that automatically eradicates data once accessed and utilized for the first time. By adopting this practice, e-commerce companies can further mitigate the risk of data breaches and safeguard their customers' confidential information.
Multi-Factor Authentication
Deploying robust security management systems is pivotal as companies aim to access data, such as credit card information, and safeguard it against cyber attacks. Multi-factor authentication (MFA) stands as one of the most effective strategies to achieve this.
Two-factor authentication (2FA) is a renowned MFA method that has shown considerable effectiveness in reinforcing security. However, the essence of 2FA is often misconstrued. To truly comprehend 2FA's functionality, one must recall this principle: the first factor is something the customer knows, such as a password, and the second factor is something the customer possesses, such as a mobile device or a one-time password sent via SMS.
If the system requests additional details, like a date of birth, it doesn't qualify as an actual "second factor" of authentication.
A multitude of e-commerce software, like Magento, already incorporates 2FA. It's worth mentioning that one-time passwords need not be transmitted solely via SMS. They can also be dispatched via instant messaging or a 2FA mobile application, often available free of charge.
Implementing MFA, particularly 2FA, is critical to securing sensitive data. Not only does it bolster protection, but it also helps to reduce the risk of unauthorized access to sensitive information. This is particularly crucial for entities that handle sensitive data and are subject to stringent information security regulations.
Furthermore, it is essential to regularly review and update information security management systems to guarantee their effectiveness in protecting sensitive data. This encompasses regular software security upgrades, monitoring suspicious activity, employing anti-malware software, and training employees about data security best practices.
Consistent Maintenance of Security Measures
Maintaining up-to-date software and security certificates is one of the most crucial tactics for securing sensitive data in cybersecurity.
Security Patches and System Updates
Regular maintenance, including security updates and patches, ensures vulnerabilities are discovered and addressed before malicious elements exploit them.
For instance, Magento, the e-commerce platform, issues such security patches monthly, tackling security vulnerabilities in the software. These patches are engineered to remedy security concerns, like those featured in the Common Vulnerabilities and Exposures (CVE) catalog, routinely updated to include the latest threats.
Although updates and patches are vital for maintaining software security, it's important to remember that cybercriminals can also infiltrate the online store through user accounts. To reduce this risk, it's advised to grant access to sensitive data strictly to those employees who require it for their tasks and only to the degree necessary for their role.
SSL Certificates
Additionally, using an SSL certificate is always included in the best practices for e-commerce security. This digital certificate verifies the legitimacy of a website and encrypts information sent to the server using SSL technology. This helps secure customers’ data, such as credit card details and login credentials, from fraudulent activities.
Security Practices
Additional security procedures include using robust passwords, avoiding reusing the same password across different services, and ensuring all staff members are trained to recognize and evade phishing scams, SQL injection, and other malevolent software.
In summary, regular updates, patches, stringent access controls, and employee training are all key elements of a holistic cybersecurity strategy.
Expert Security Testing

As cyber threats evolve, e-commerce websites must proactively safeguard sensitive data and systems from malevolent code and attacks.
Understanding Penetration Testing
A crucial part of this is penetration testing, often termed "ethical hacking," which involves simulating hackers' attacks on a computer system to uncover vulnerabilities that malevolent entities might exploit.
Penetration testing is a detailed and nuanced procedure, typically executed by a dedicated team of e-commerce security professionals. The testing process encompasses many potential threats, like brute force attacks, DDoS attacks, and other forms of malevolent code.
The process simulates the most prevalent attacks, such as those listed in the OWASP Top 10, a globally recognized list of the world's top 10 vulnerabilities.
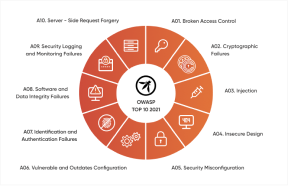

The main objective of penetration testing is to identify vulnerabilities and weaknesses in a company's systems and infrastructure and offer solutions to rectify them.
The testing process should also yield a detailed report indicating what areas of the system have passed a successful check, which areas need extra attention, and where issues need urgent rectification.
Understanding that penetration testing is only one facet of a comprehensive cybersecurity strategy is crucial. A multi-layered security approach that includes a secure environment and monitoring critical systems is essential to protect companies against a broad spectrum of potential threats.
In conclusion, penetration testing is vital to any company's cybersecurity strategy and should be a consistent part of the overall security review process. Companies can uncover vulnerabilities and take measures to address them by simulating attacks.
Moreover, a multi-layered security approach and SSL certificates are critical to safeguarding the company from malicious code and attacks, offering a secure environment, and monitoring critical system.
The Significance of a Contingency Plan: Actions to Take if a Cyber Attack Succeeds?

For an online business, the security of your online e-commerce platform is paramount. However, despite all the security measures you implement, there always remains a risk of a breach. Therefore, it's vital to have a contingency plan ready if the system has been compromised.
Security Backup and Recovery
One of the most critical measures is automating data backup and recovery processes. This guarantees you will retain a copy of your customer and order database and other crucial business data even during a breach.
Having a backup or test server in place to use in case of a security incident is also critical. This allows you to rapidly restore your site and minimize the impact of a security breach.
Service Level Agreement
Another critical aspect of e-commerce security is establishing a Service Level Agreement (SLA) with a technical contractor. This ensures the quality of service in the event of a malicious attack on your site.
In our SLA at Perspective, we specify:
- A fixed response time in case of a security incident
- A set time for a quick resolution.
- A defined time for a permanent resolution.
For example, the agreement might specify that the contractor must restore the site's functioning within 2 hours, regardless of whether it happened during business hours or outside of them.
Additionally, it is essential to enlighten employees and customers about suspicious links, phishing, and cyber-attacks, to detect and report them. This can help lessen the risk of cyber-attacks and minimize the impact of any incident.
In conclusion, protecting your online business from security breaches is a continuous process requiring a multi-layered approach. Automating data backup and recovery processes, having a backup server, and an SLA with a technical contractor can ensure that your online e-commerce store is prepared to respond promptly and effectively during a breach. Moreover, educating employees and customers is essential to detect and report suspicious links.
Final Remarks
As the world shifts towards online commerce, shielding e-commerce sites from attacks grows increasingly critical. Given the vast amounts of personal and financial data stored on these platforms, any e-commerce website must secure its customers' information. Data breaches remain one of the most common threats to e-commerce site security.
Usual e-commerce security threats include hacking, phishing, cross-site scripting, and third-party integrations. Companies must implement robust data protection measures like encryption, firewalls, and intrusion detection systems to mitigate these risks.
Another vital consideration for any e-commerce website is compliance with regulations like the General Data Protection Regulation (GDPR). This law, which took effect in the EU in 2018, establishes strict standards for handling personal data and imposes heavy fines for non-compliance.
Non-compliance with the GDPR can result in fines as high as 2-5% of the company's annual turnover, making it crucial for companies conducting online sales to understand and comply with the regulation to protect their customers and profits.
Companies must be proactive to stay ahead of the curve in e-commerce security. This means selecting responsible partners and contractors, regularly testing systems and protocols, and staying informed about the latest threats and trends in the field. By taking these steps, companies can ensure that their customers' data is safe and that their businesses are protected from expensive breaches and penalties.
Get Your Cybersecurity Audit Today
Perspective article collection
If you would like to read more articles on eCommerce best practices, here they are for you:
-
Magento Security Best Practices: A Comprehensive Guide to Secure Integrations
-
Best Managed Magento Hosting Platforms
-
Magento ERP Integration: Unify and Optimize Ecommerce Operations
-
Six Strategies That Can Increase Average Order Value by Up to 50%
-
Boosting Your E-commerce Visibility: A Comprehensive Guide to Magento SEO Audit
-
A Synergy Story: Blending ChatGPT's AI Capabilities with Magento's E-commerce Excellence
-
Magento Security Audit: Ensuring the Safety of Your E-commerce Store
-
Enhancing Your E‑commerce Performance: A Comprehensive Guide to Magento Performance Audit
-
Easier than you think: Magento 2 Integration with CRM system


